Resolving the security ‘Missing X-XSS-Protection’ header issue

Today in this article, we shall see how to resolve security vulnerabilities like ‘Missing X-XSS-Protection‘.
Today we will cover the below aspects,
The HTTP X-XSS-Protection is a header and type of response header. It is a feature of most common browsers including Internet Explorer, Chrome, and Safari which helps to enable cross-site scripting in the browser.
Why use a response header – X-XSS-Protection
If a malicious input is being injected into the browser, this header lets your browser define action. If a cross-site scripting attack is detected, the browser will sanitize the page and the malicious part will either be removed OR the browser will prevent rendering of the page and will block an attack (mode=block).
Syntax
Below are the four options for enabling Cross-site scripting.
X-XSS-Protection: 0X-XSS-Protection: 1X-XSS-Protection: 1; mode=blockX-XSS-Protection: 1; report=<report-uri>
X-XSS-Protection: 0
Disables XSS filtering.
X-XSS-Protection: 1
- Enables Cross-site scripting (XSS) filtering.
- This is the default option used by most browsers if the setting is not specified explicitly.
- If a cross-site scripting attack is detected, the browser will sanitize the page and the malicious/unsafe part will be removed.
X-XSS-Protection: 1; mode=block
- Enables Cross-site scripting (XSS) filtering.
- Enable the built-in XSS protection, and block an attack (mode=block).
- The browser prevents the rendering of the page.
X-XSS-Protection: 1; report=<report-Uri>
- Enables Cross-site scripting (XSS) filtering.
- If a cross-site scripting attack is detected, the browser will sanitize the page and report the violation.
- The report will be sent to <report-URI>
For ASP.NET Core below is the code of how I have added the X-XSS-Protection” header using the middleware component,
app.Use(async (context, next) =>
{
context.Response.Headers.Add("Content-Security-Policy", "default-src 'self';");
context.Response.Headers.Add("X-Content-Type-Options", "nosniff");
context.Response.Headers.Add("X-XSS-Protection", "1");
context.Response.Headers.Add("Strict-Transport-Security", "max-age=31536000 ; includeSubDomains");
await next.Invoke();
});
Please use a similar technique to fix the issue in any coding language like python, java, etc.
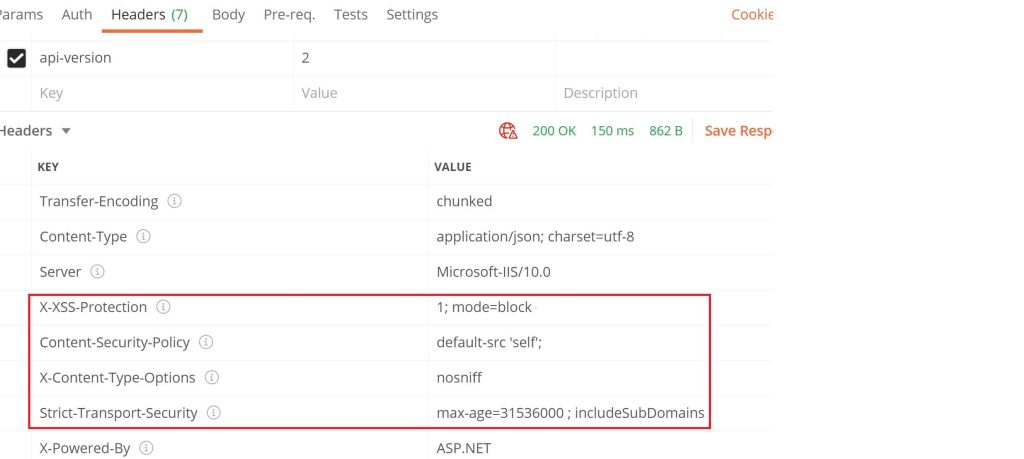
Once enabled, you shall see the response with XSS header,
References :
Do you have any comments or ideas or any better suggestions to share?
Please sound off your comments below.
Happy Coding !!
Please bookmark this page and share it with your friends. Please Subscribe to the blog to receive notifications on freshly published(2024) best practices and guidelines for software design and development.